Separating Data Example 1
For this example, we have three users in our user table: Steph, Klay, and Jordan.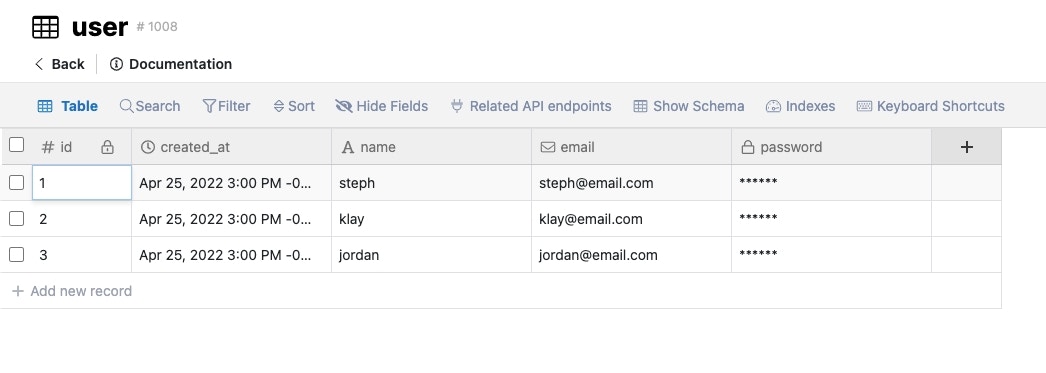
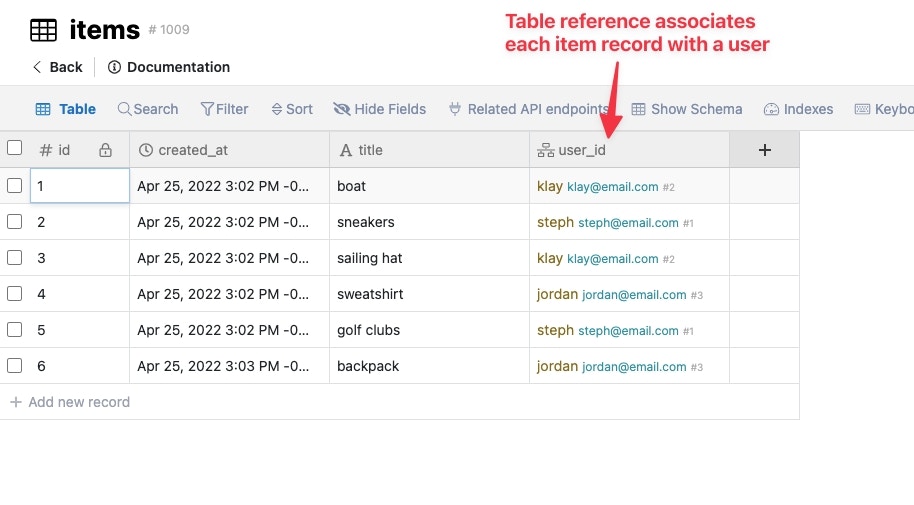
How to enforce a user only sees the items that belongs to them
Here we have an API endpoint, which gets all the items from the items table. The first step is to require user authentication on the endpoint.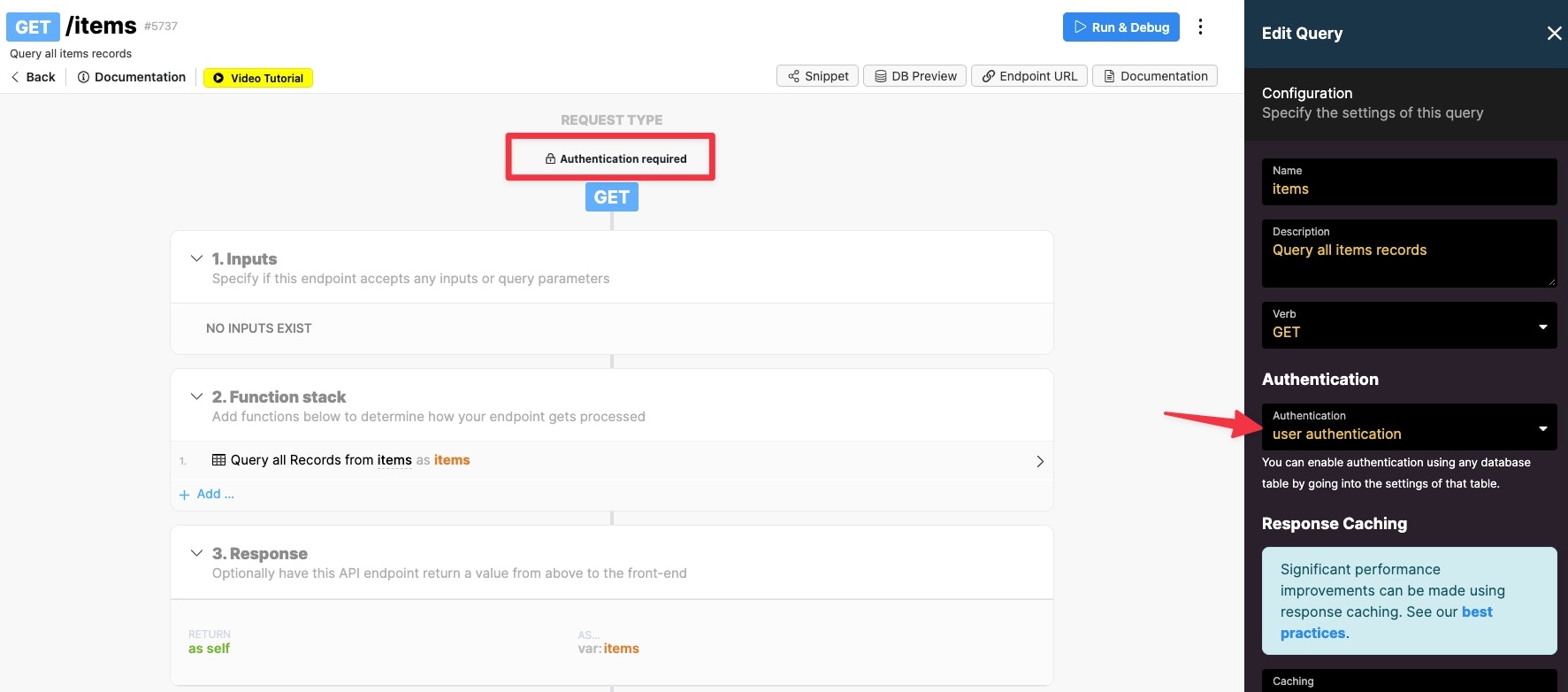

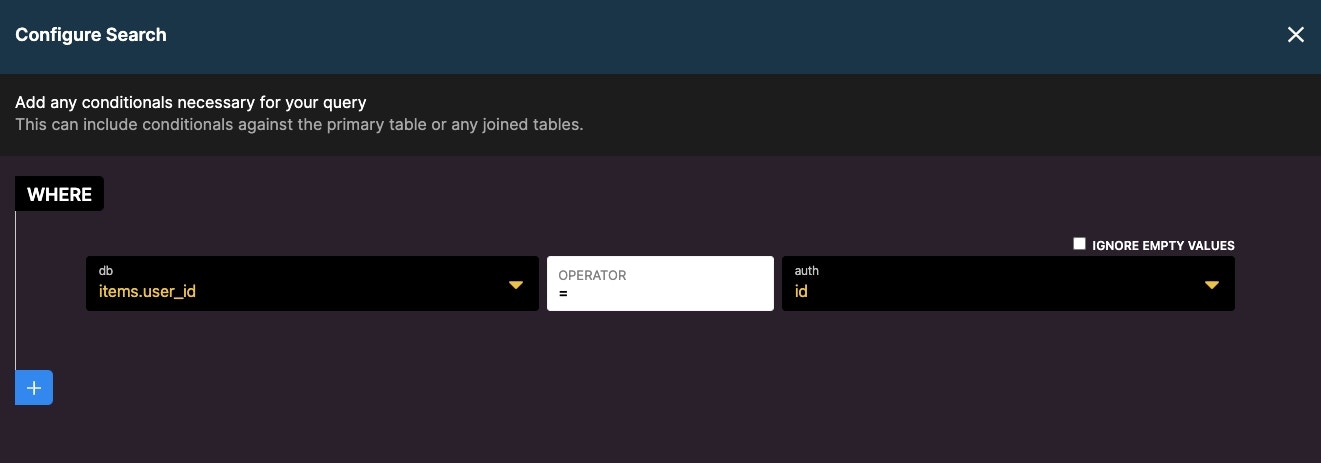
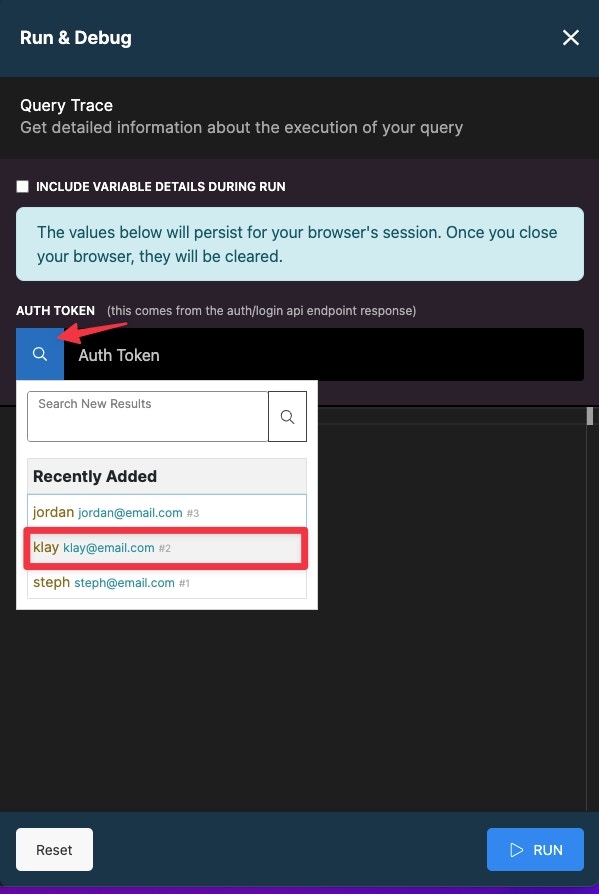
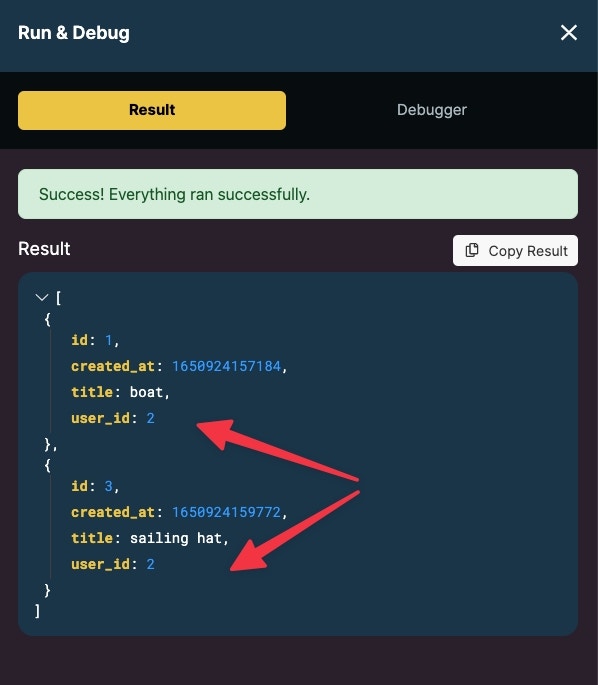
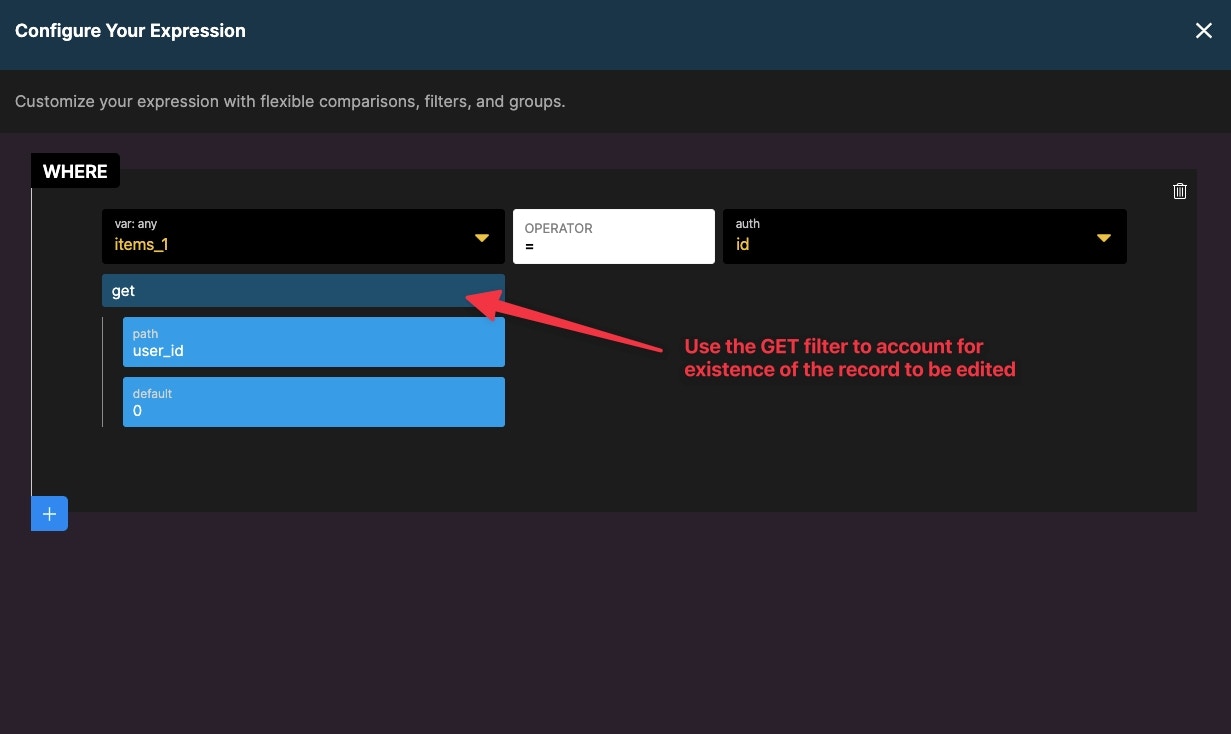
Added layer of security with precondition
We can add an additional layer of security with the use of preconditions. First, use a Get Record on the user table with a field value of the auth id.
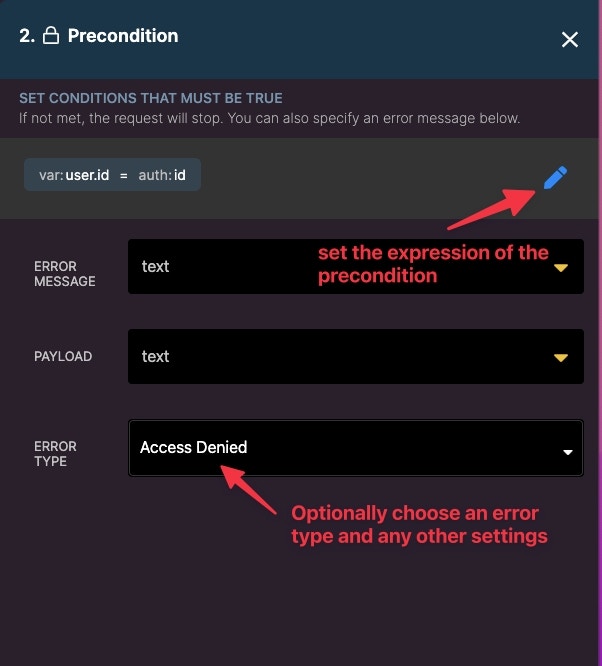
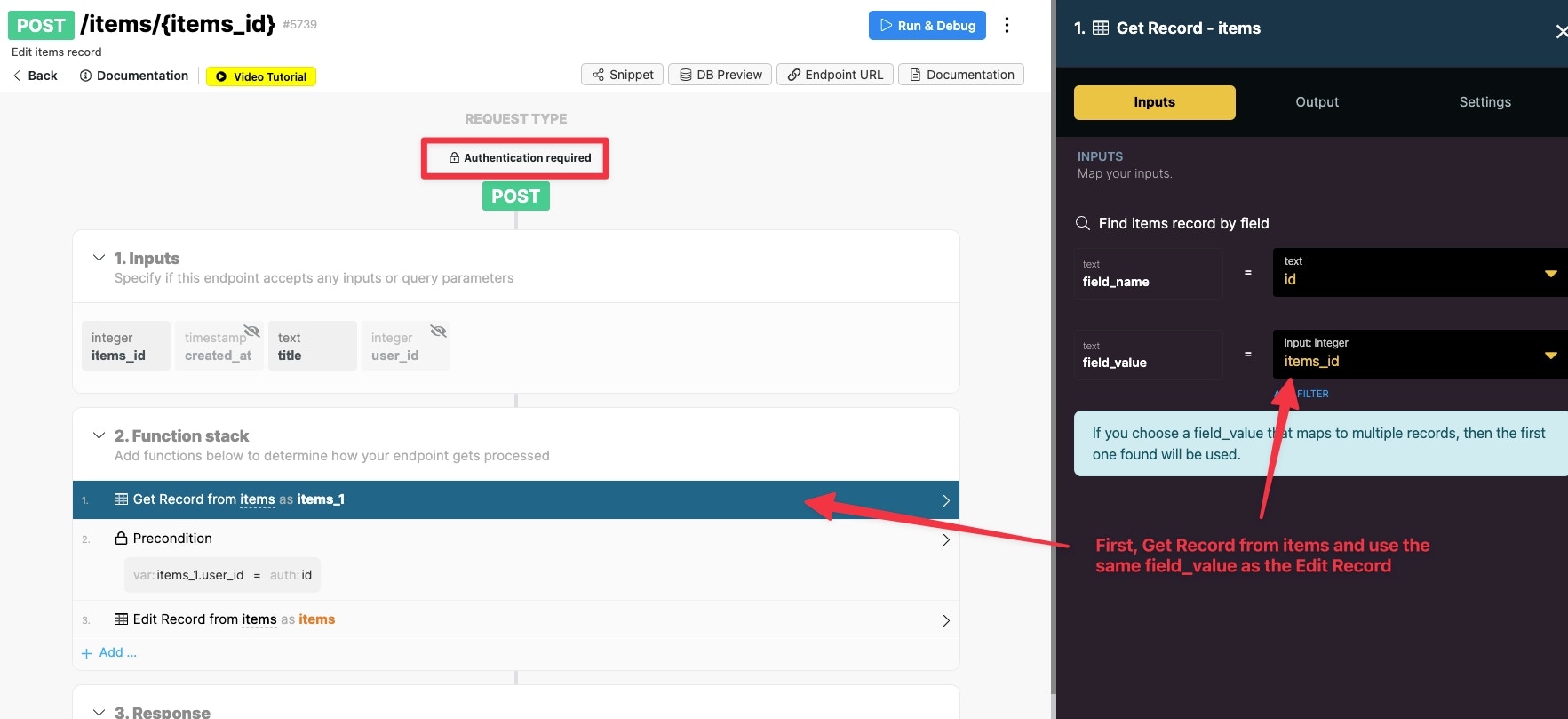
How to enforce the user can only edit data that belongs to them
When it comes to editing data, the function stack will also use a precondition. The API endpoint will once again require authentication. First, we need to Get the Record of the item that the user wants to edit.