Authentication
Authentication is handled by JWE tokens, which is an industry standard. Authentication is how a user logs in or signs up to an application. Xano provides secure out-of-the-box authentication via JWE (JSON Web Encryption) tokens. JWE tokens are self-contained and provide data integrity, authenticity, non-repudiation, and confidentiality. OAuth, which stands for “Open Authorization,”** allows third-party services to exchange your information without you having to give away your password.** **OAuth **providers such as Facebook, Google, LinkedIn, and GitHub login are available in the Xano marketplace to easily enable.Single-Tenancy
On Xano’s dedicated resource plans, the user’s Instance is on a single-tenant deployment or architecture. This means that the user is the only tenant on the server (Instance) architecture and that all the server resources and CPU are dedicated to the tenant. Single-tenancy has a variety of benefits including: **Data Separation **- Data is kept separate from other users since the Instance is isolated. This allows for independence of data and greater customization of software and hardware. Data Security - If one user has a breach of data, then another user is safe from the breach since their data is stored on a completely separate Instance. Reliability & Performance - Since the Instance is only dependent and serves a single tenant, performance and reliability are significantly increased. The alternative would be the Instance serving many different users. Recovery - With a single-tenancy backups are also isolated, making it easier and more reliable to restore from backups in the event of a disaster.Password Requirements
Xano requires password minimums for logging in to a Xano account. A password must be a minimum of eight (8) characters, maximum of 256 characters, at least one (1) alphabetic character, and at least one (1) numeric character. These password requirements are only for login by email and password. Password requirements for Single Sign-On (SSO) are managed by the SSO provider.2FA Security
Two-factor authentication (2FA) security, or two-step authentication, can be enabled for logging in to a Xano account. 2FA security requires the use of two different forms of identification to access and authenticate an account. It is an extra layer of security beyond email and password credentials that secures an account by requiring an authentication step from something that belongs to the user. 2FA security can be enabled from the account page of a Xano account. Learn how to enable 2FA.Inactivity Timeout
To protect your privacy, Xano includes an inactivity timer which will log you out after 2 hours of inactivity by default, but this can be adjusted or disabled entirely via your account settings. This is based on mouse activity and works across multiple tabs.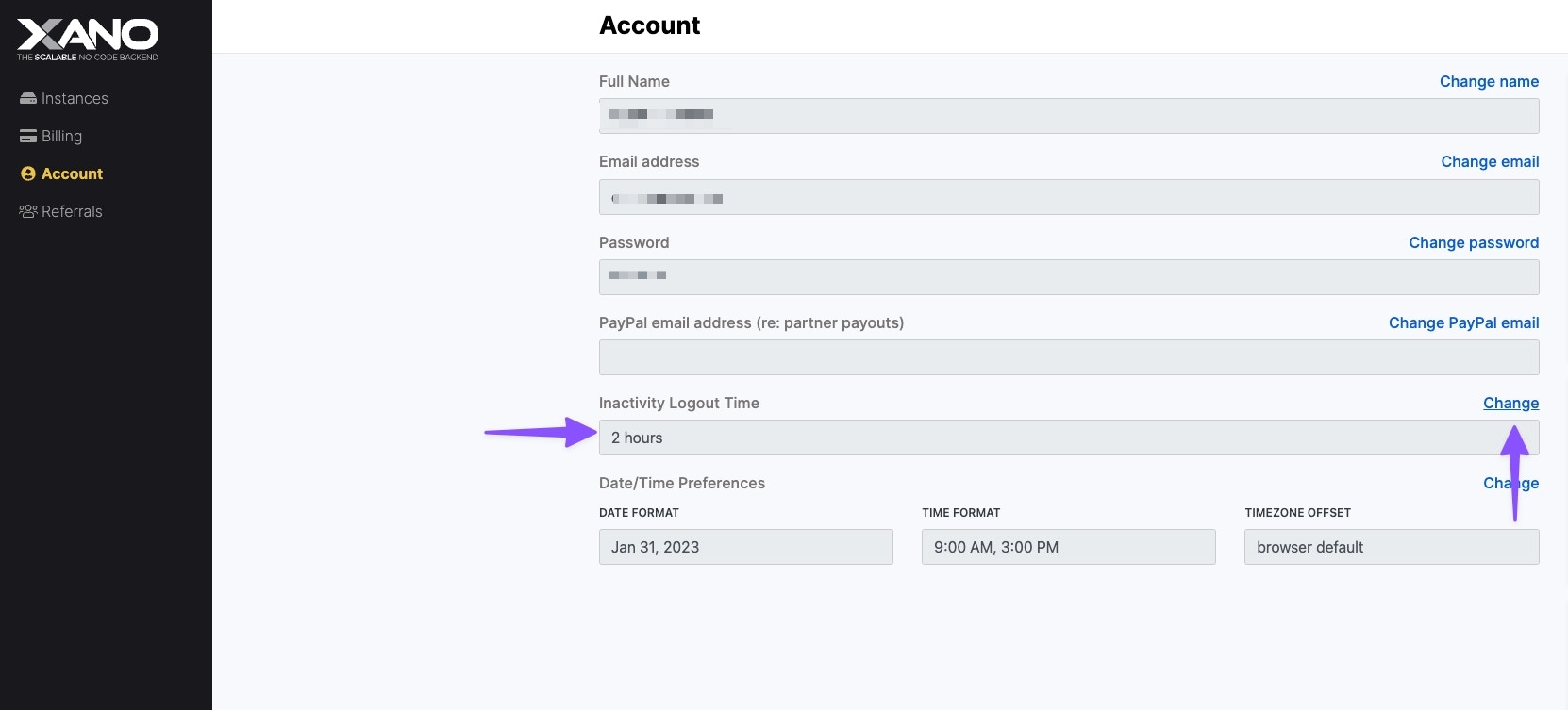
Enforcement
On certain Xano plans, you have the ability to enable security policy enforcement through your Instance settings.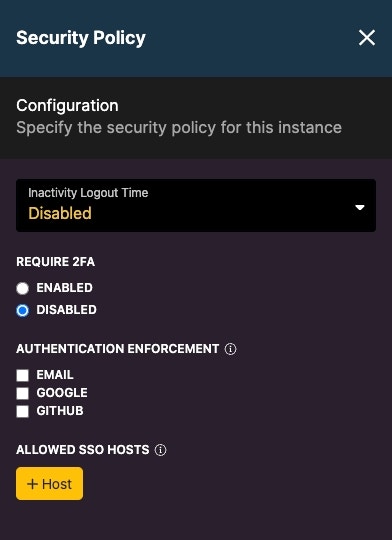
Sensitive Data Flagging
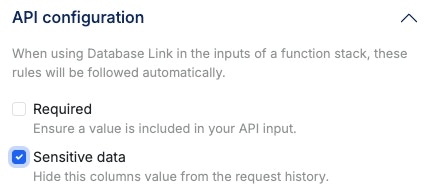
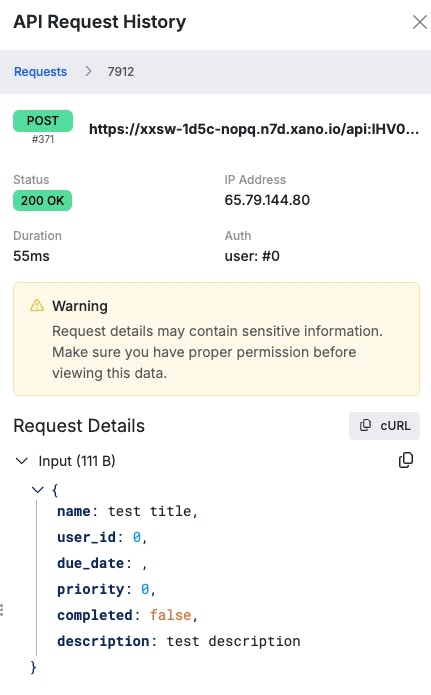
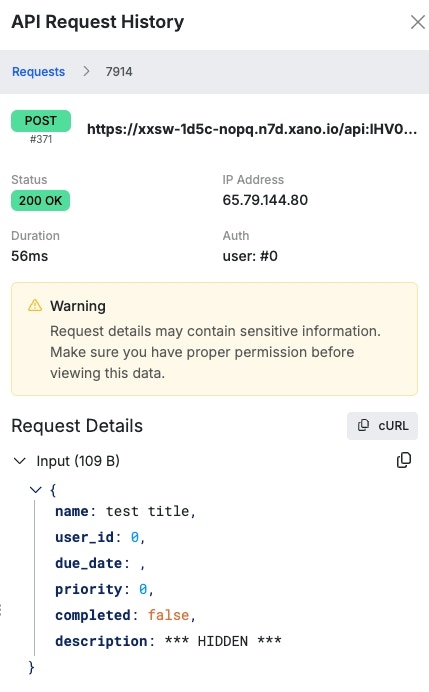
Xano maintains a request history of incoming requests of your APIs. To ensure that no sensitive data is not logged in the request history, you can enable the Sensitive Data flag on that database field to ensure it is not stored.The sensitive data flag only impacts the inputs of a request when using database link, which automatically creates inputs for you based on database fields; you will want to ensure that the sensitive data is not returned elsewhere in your function stack.