- create_uid - Returns a unique 64bit unsigned int value seeded off the value.
- decrypt - Decrypts the value and returns the result.
- encrypt - Encrypts the value and returns the result.
- hmac_md5 - Returns a MD5 signature representation of the value using a shared secret via the HMAC method
- hmac_sha1 - Returns a SHA1 signature representation of the value using a shared secret via the HMAC method
- hmac_sha256** / hmac_sha384 / hmac_sha512** - Returns a SHA256/384/512 signature representation of the value using a shared secret via the HMAC method
- jwe_decode - Decodes the value represented as JWE token and returns the original payload.
- jwe_encode - Encodes the value and returns the result as a JWE token.
- md5 - Returns an MD5 signature representation of the value.
- secureid_decode - Returns the id of the original encode.
- secureid_encode - Returns an encrypted version of the id.
- sha1 - Returns a SHA1 signature representation of the value.
- sha256 / sha384 / sha512 - Returns a SHA256/384/512 signature representation of the value.
create_uid:
Returns a unique 64bit unsigned int value seeded off the value.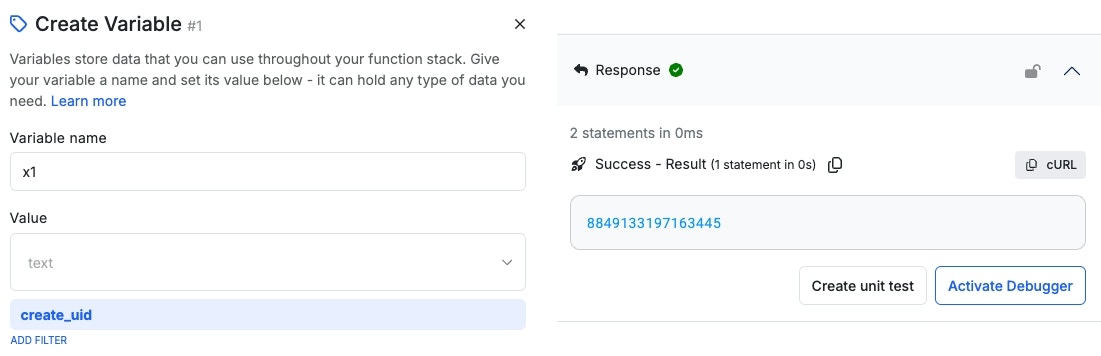
decrypt:
Decrypts the value and returns the result.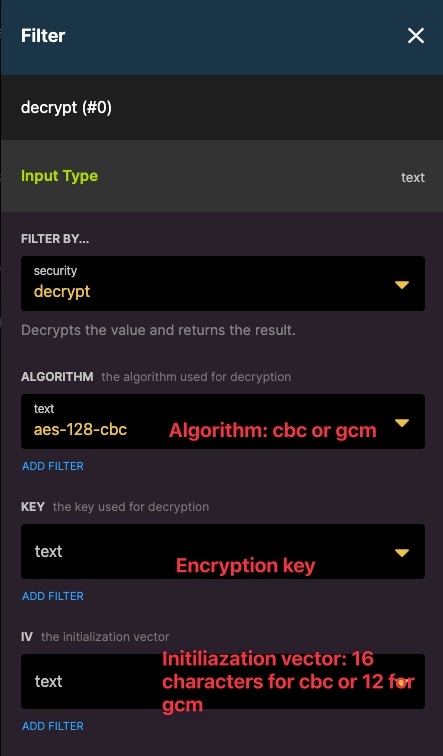
encrypt:
Encrypts the value and returns the result in raw binary form. Find more details on the encrypt function page.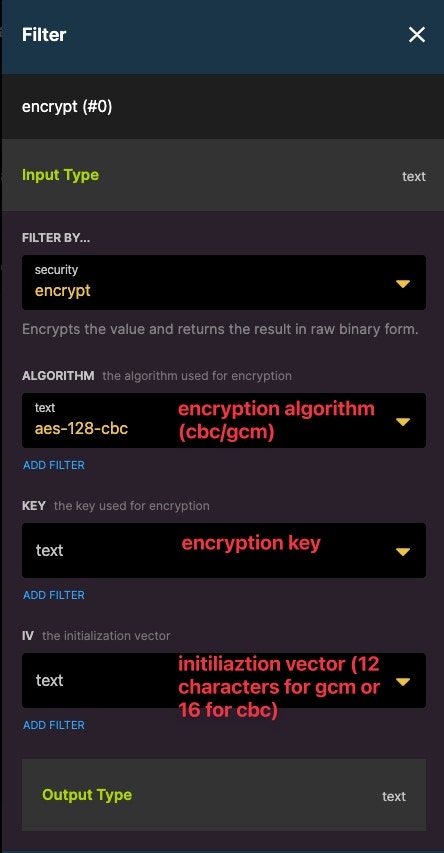
hmac_md5
Returns a MD5 signature representation of the value using a shared secret via the HMAC method. The secret key is a unique piece of information that is used to compute the HMAC and is known both by the sender and the receiver of the message. This key will vary in length depending on the algorithm that you use.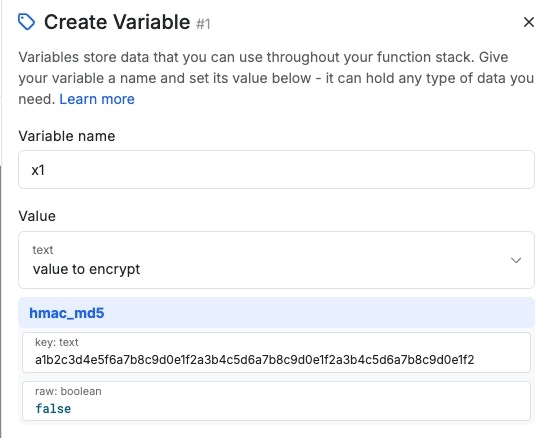
hmac_sha1
Returns a SHA1 signature representation of the value using a shared secret via the HMAC method. The secret key is a unique piece of information that is used to compute the HMAC and is known both by the sender and the receiver of the message. This key will vary in length depending on the algorithm that you use.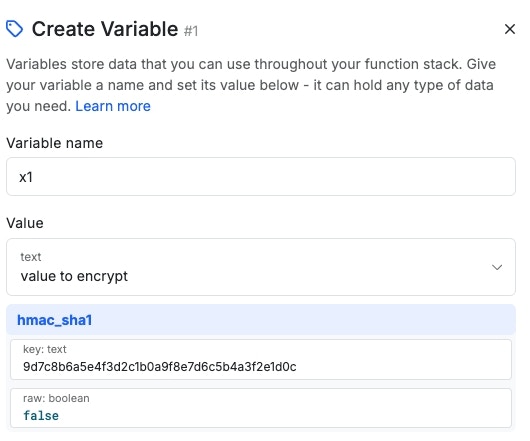
hmac_sha256 / hmac384 / hmac512
Returns a SHA256/384/512 signature representation of the value using a shared secret via the HMAC method. The secret key is a unique piece of information that is used to compute the HMAC and is known both by the sender and the receiver of the message. This key will vary in length depending on the algorithm that you use.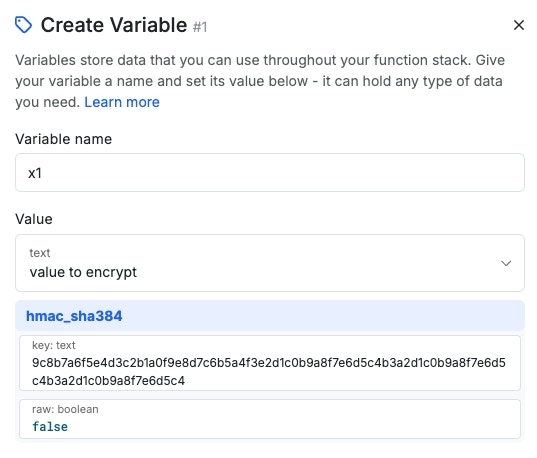
jwe_encode / jwe_decode:
Encodes the value and returns the result as a JWE token. HEADERS: Any custom headers to include in the JWE token Sample:{"kid": "12345"}
KEY: The encryption key for the JWE token Sample: a1b2c3d4e5f6a7b8c9d0e1f2a3b4c5d6
KEY_ALGORITHM: Choose one of the algorithms used to encode the token.
CONTENT_ALGORITHM: Choose one of the algorithms used to encode the token.
TTL: Token expiration time in seconds Sample: 3600 (1 hour), 0 means no expiration
md5
Returns an MD5 signature representation of the value. A salt value can be added to the text to provide an extra layer of security.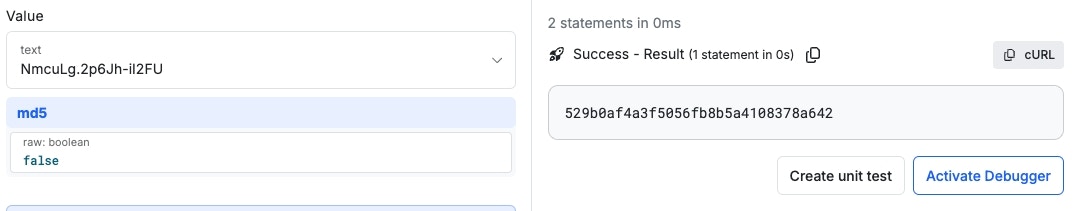
secureid_decode
Returns the id of the original encode. If a salt was added to encode this value the same salt needs to be added to decrypt it.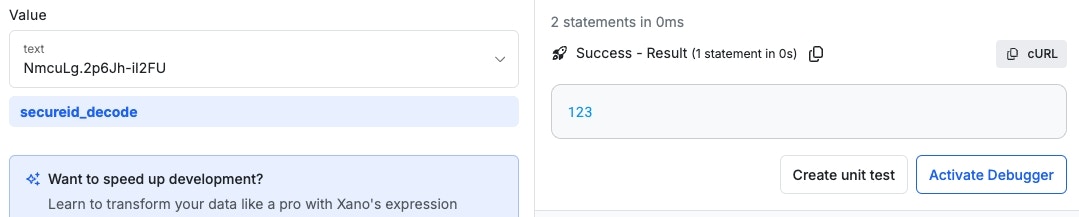
secureid_encode
Returns an encrypted version of an integer. A salt value can be added to the text to provide an extra layer of security.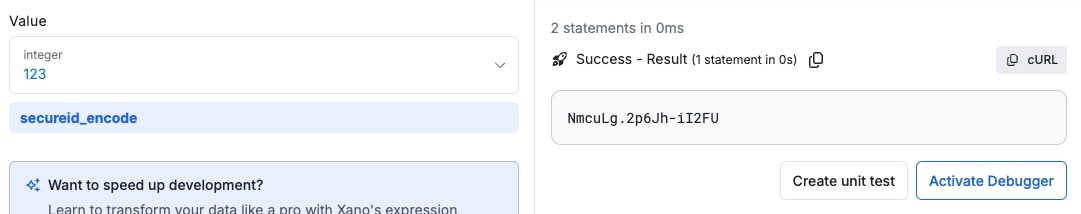
sha1 / sha256 / sha384 / sha512
Returns a SHA1 signature representation of the value. A salt value can be added to the text to provide an extra layer of security.