Skip to main contentSecurity functions are a mix of helper functions and cryptography/encryption functions to bring added security to your function stack and application.
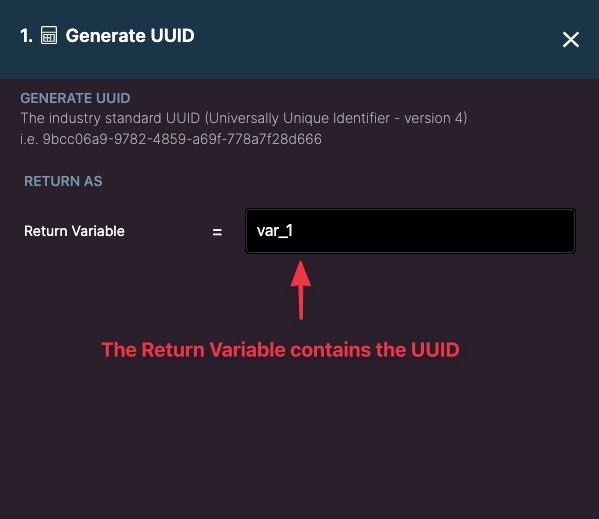
UUID
Generate a globally unique identifier. The industry standard UUID (Universally Unique Identifier - version 4) i.e. 9bcc06a9-9782-4859-a69f-778a7f28d666
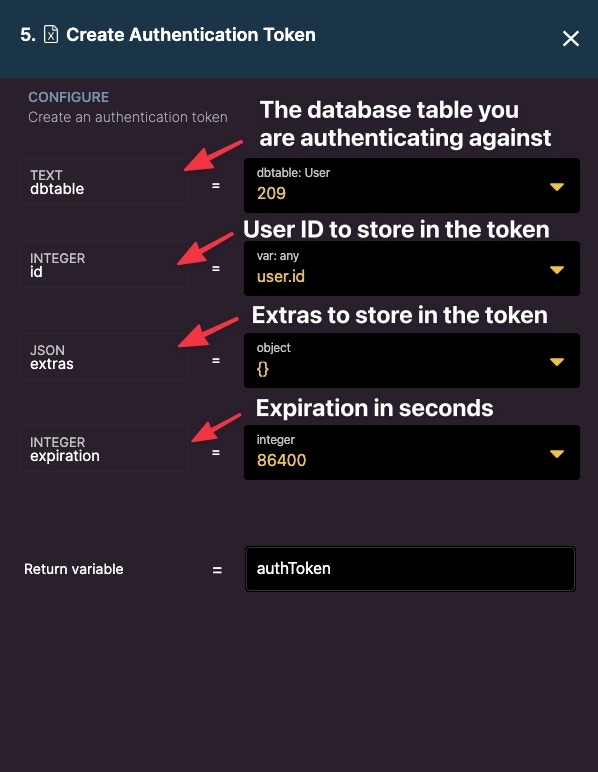
Create Authentication Token
Create a Token used for Authentication. Authentication is an important concept in app building, you can read more about it here.
- dbtable: Refers to a database table that has authentication enabled. Select the table you wish to authenticate against
- id: The ID to be stored in the token. Typically, this is a user ID, which you will get from a user record.
- extras: Extras allow you to store additional data in the authentication token. An example of this may be a user’s role. Use the SET filter to define a path and the value of the extra. Read more about extras.
- expiration: The amount of time, in seconds, the authentication token will last. You can set this to a very large number if you don’t plan on having the token expire.
- Return variable: Contains the output of the created authentication token.
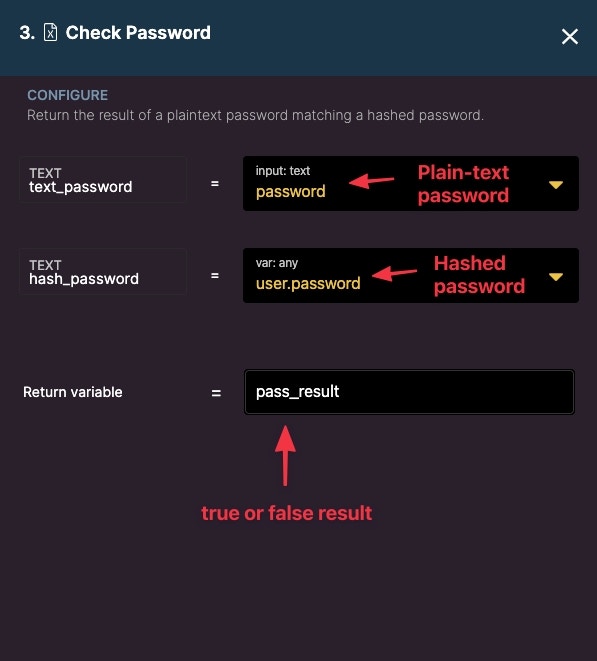
Validate (Check) Password
Return the result of a plaintext password matching a hashed password.
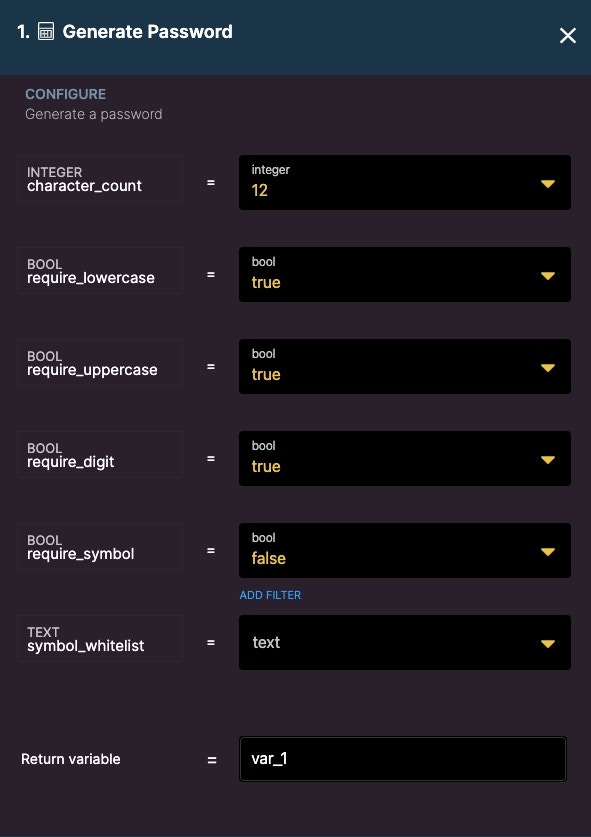
Generate Password
Generates a password.
- character_count - Number of required characters
- require_lowercase - True/false if lowercase characters are required.
- require_uppercase - True/false if uppercase characters are required.
- require_digit - True/false if a numerical digit is required.
- require_symbol - True/false if special symbols are required.
- symbol_whitelist - Optionally whitelist a symbol.
- Return variable - Returns the generate password in a variable.
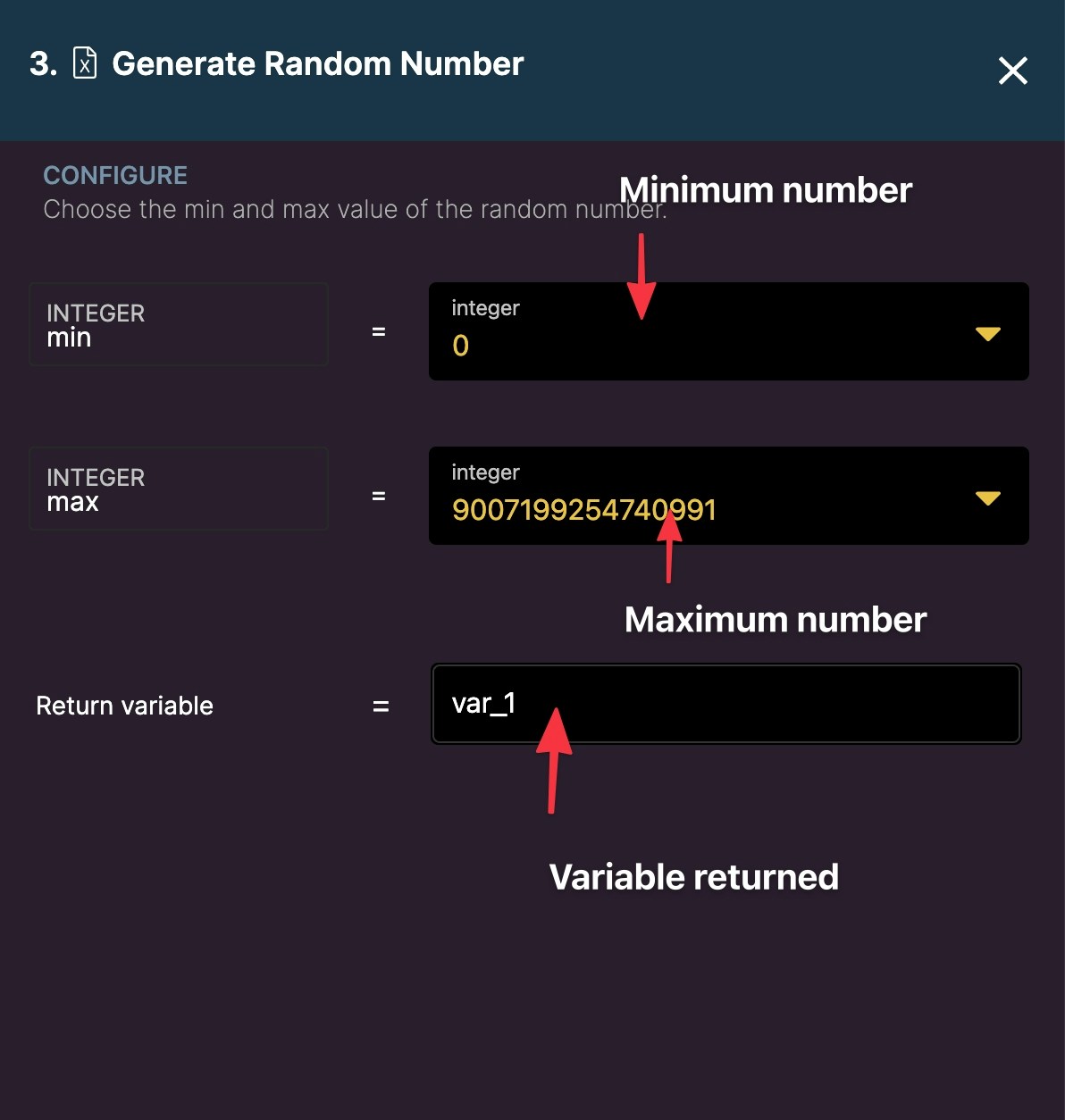
Random Number
Generate a random number.
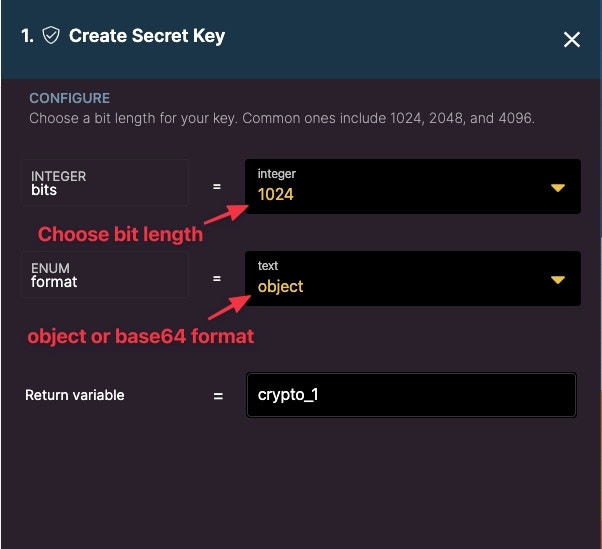
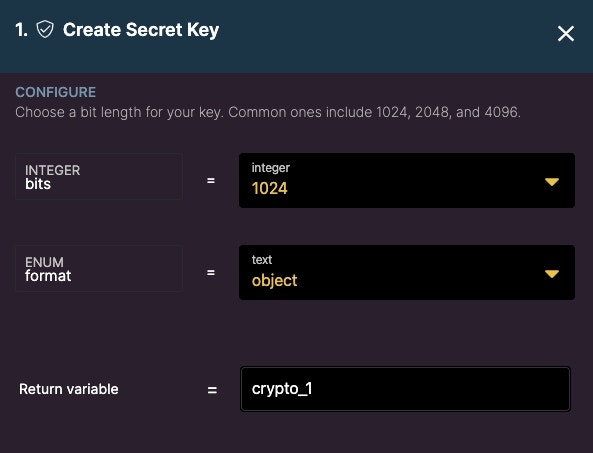
Create Secret Key
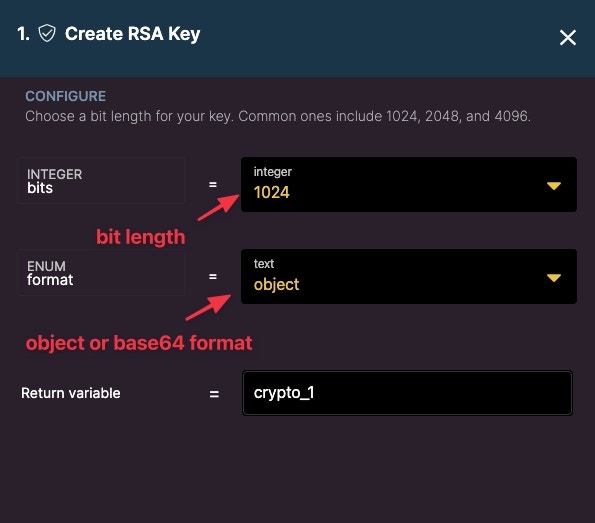
Create RSA Secret
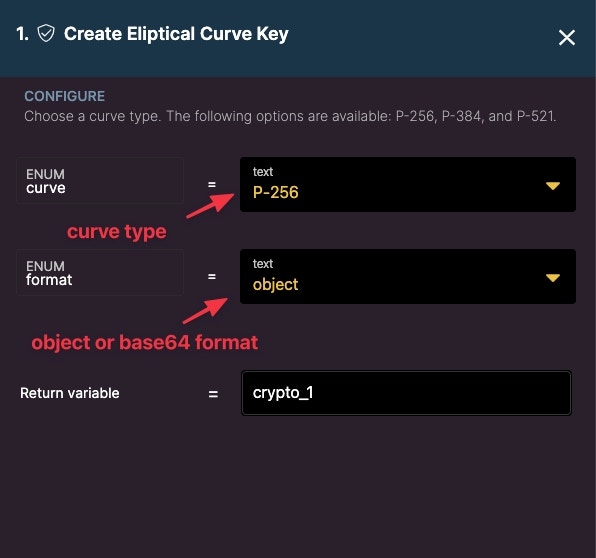
Create Elliptic Curve Key
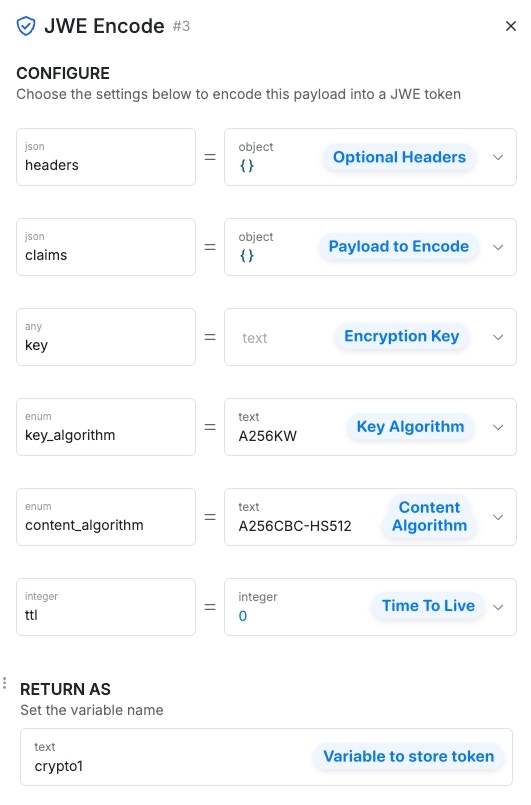
JWE Encode
Encode a payload as a JWE token.
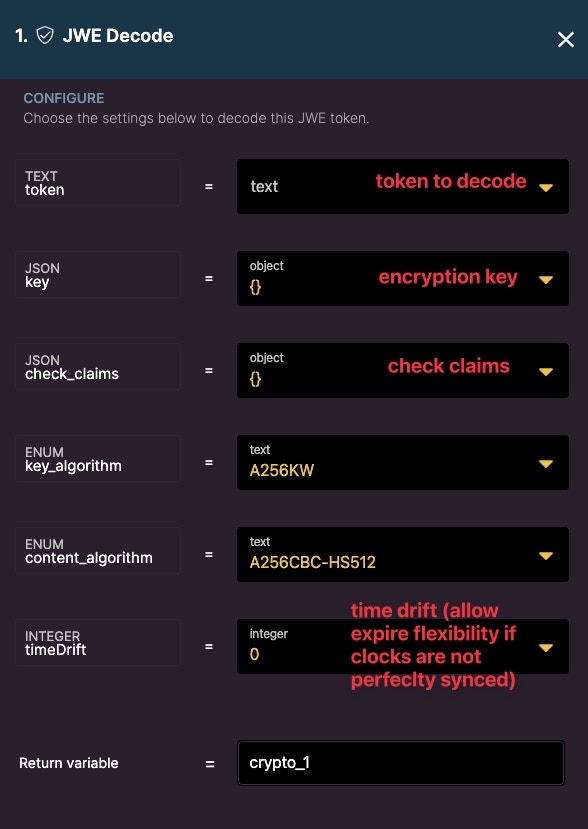
JWE Decode
Decode a JWE token.
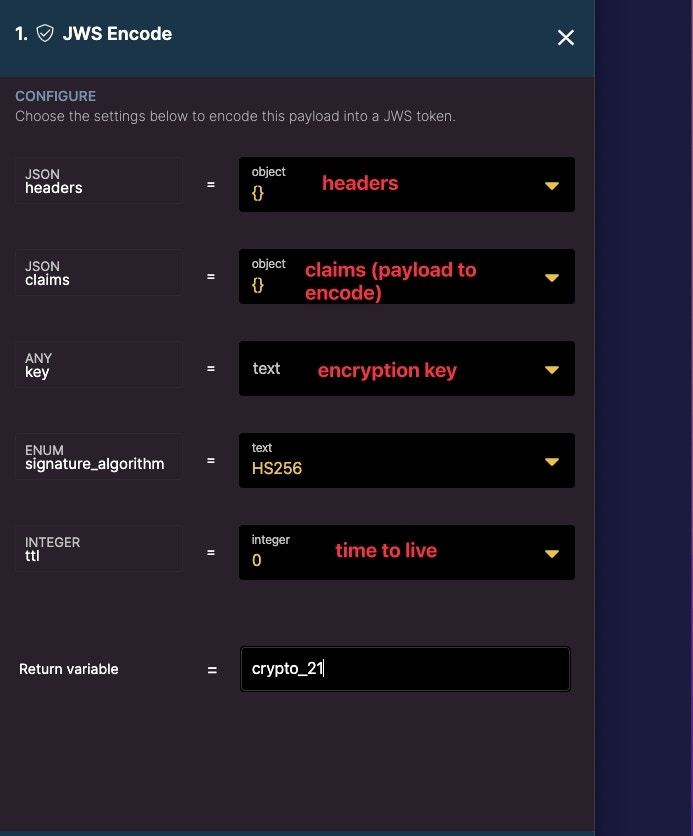
JWS Encode
Encode a payload as a JWS token.
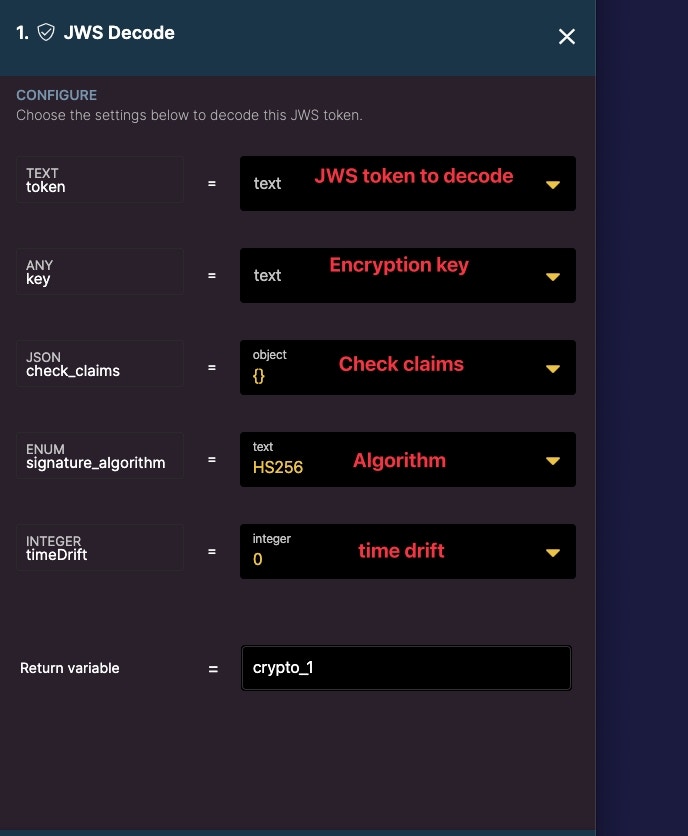
JWS Decode
Decode a JWS token.
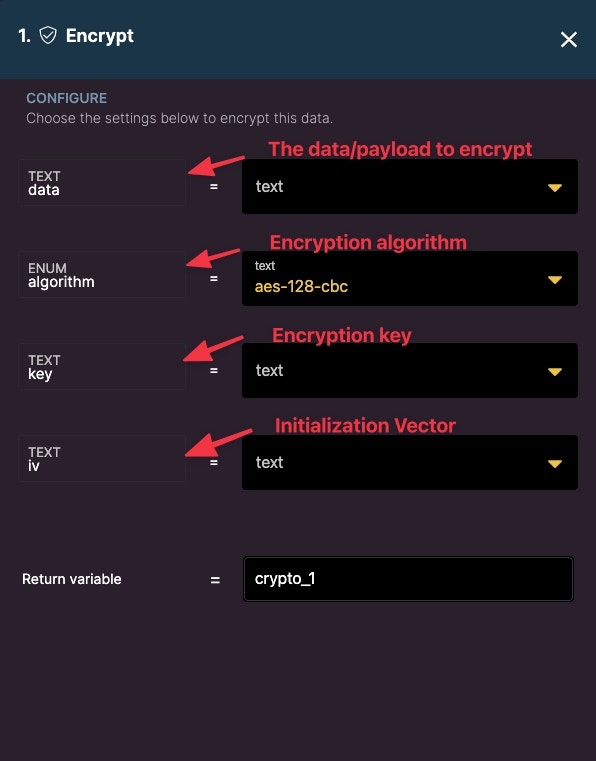
Encrypt
Encrypt a payload as raw binary data.
- Data - add the data or payload that you want to encrypt
- Algorithm - choose between six algorithms (cbc or gcm)
- Key - A key can be generated from one key generating function or you can insert raw text as your key. This same key will be needed to decrypt the data.
- IV - This is either 16 or 12 characters depending on your algorithm (cbc requires 16 characters and gcm requires 12). This information should be kept hidden in an env variable. If you are sending encrypted data to someone, then they would need to know this.
Tip: For certain use cases when passing the encrypted value through a URL, it is recommended to use the base64_encode_urlsafe filter.
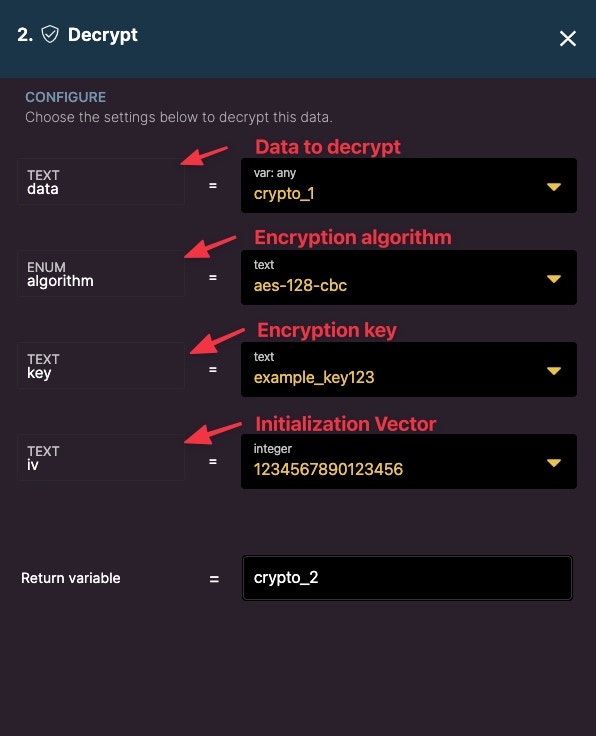
Decrypt
Decrypt a payload to its original form.
Examples
JWS Encode/Decode Example
Using your own key
We can use our own encryption key when encoding and decoding JWS.
First, use the Create Secret Key function to generate a secret key.
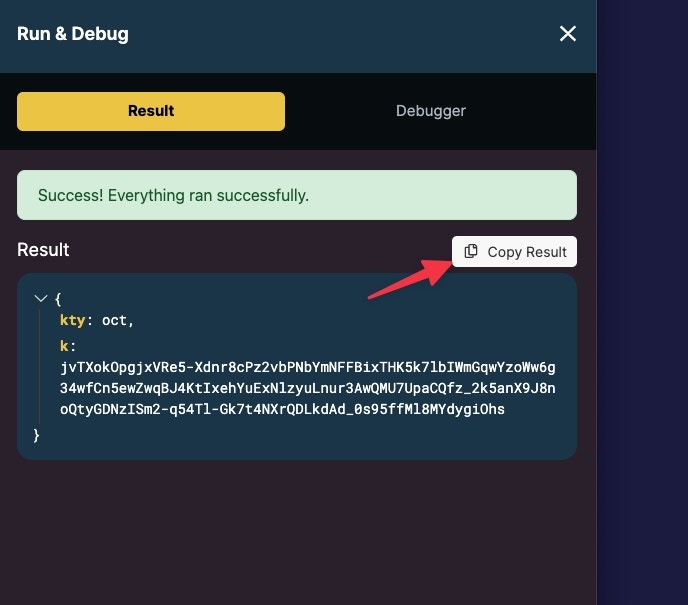
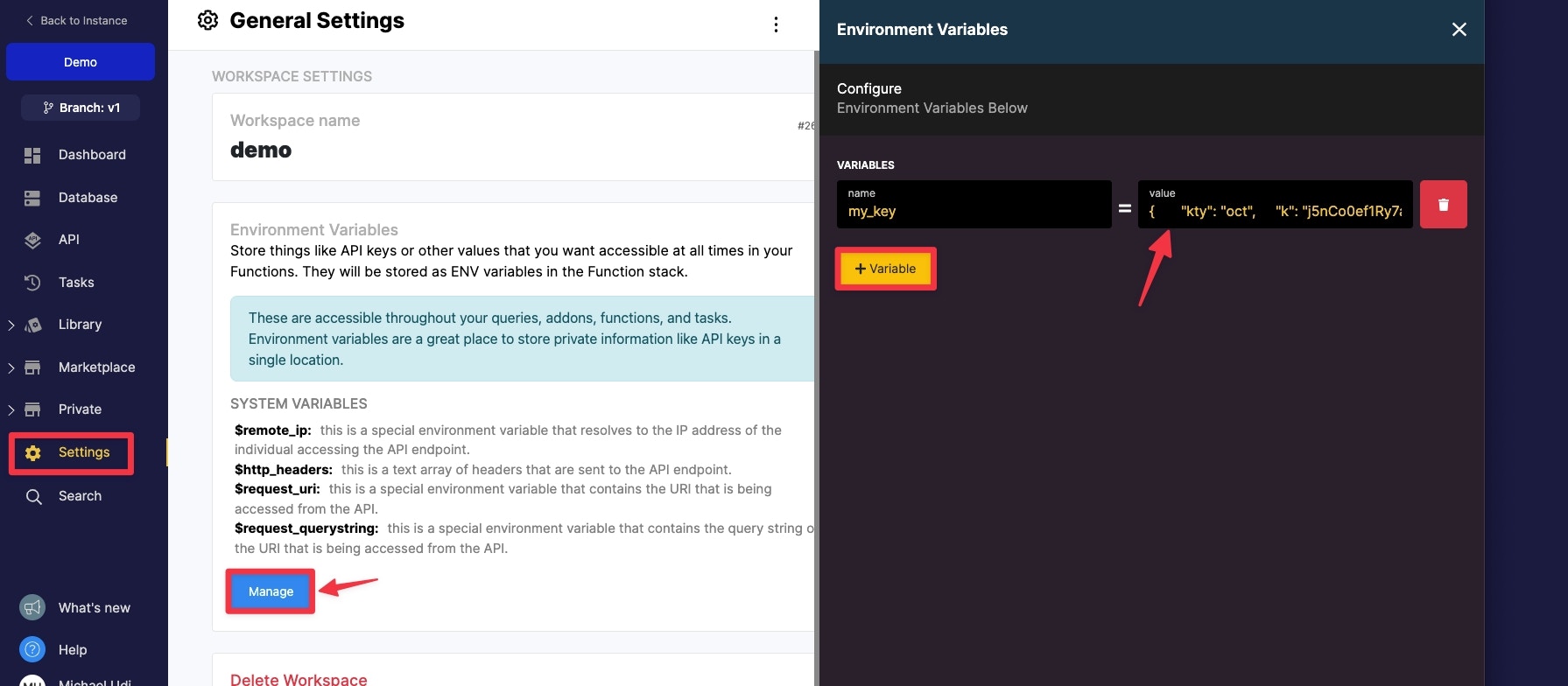
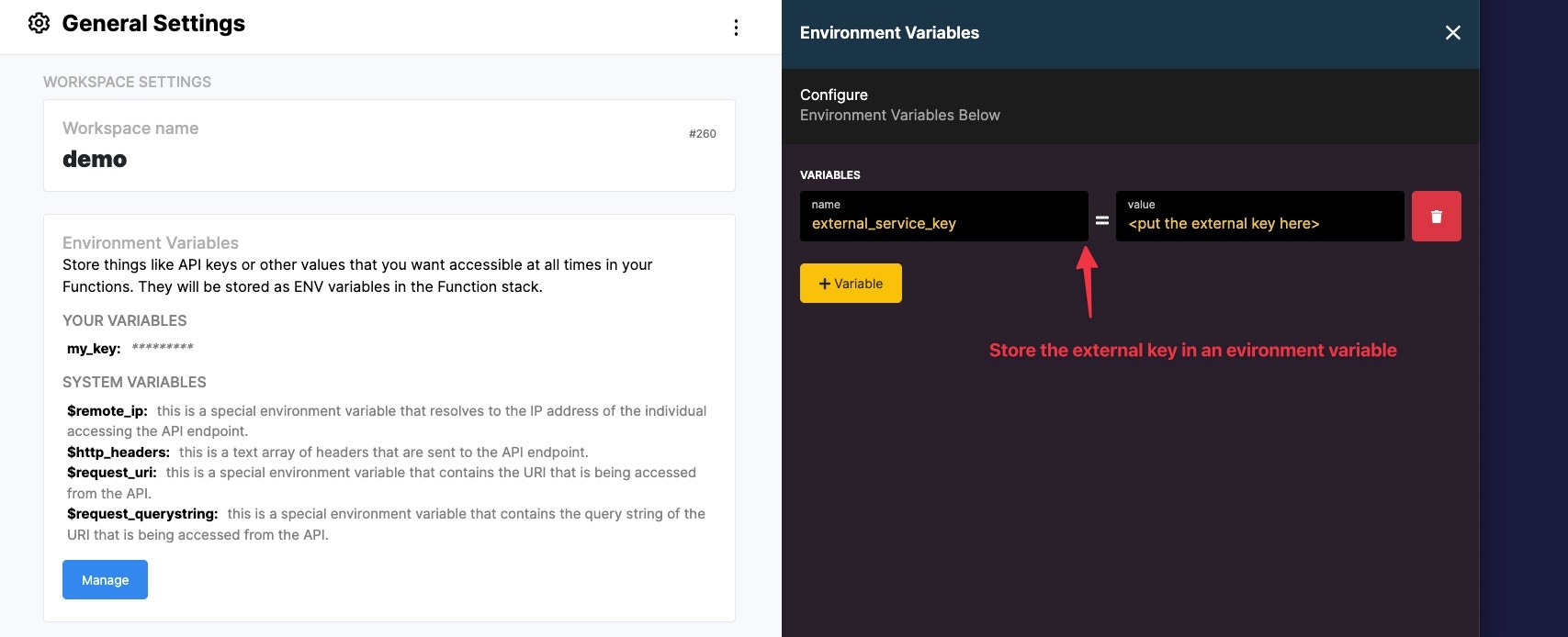
It’s a good idea to store the key in a safe, reusable place such as in an environment variable. Click the copy result button on the result of the secret key.
Navigate to the settings page and add your secret key as an environment variable.
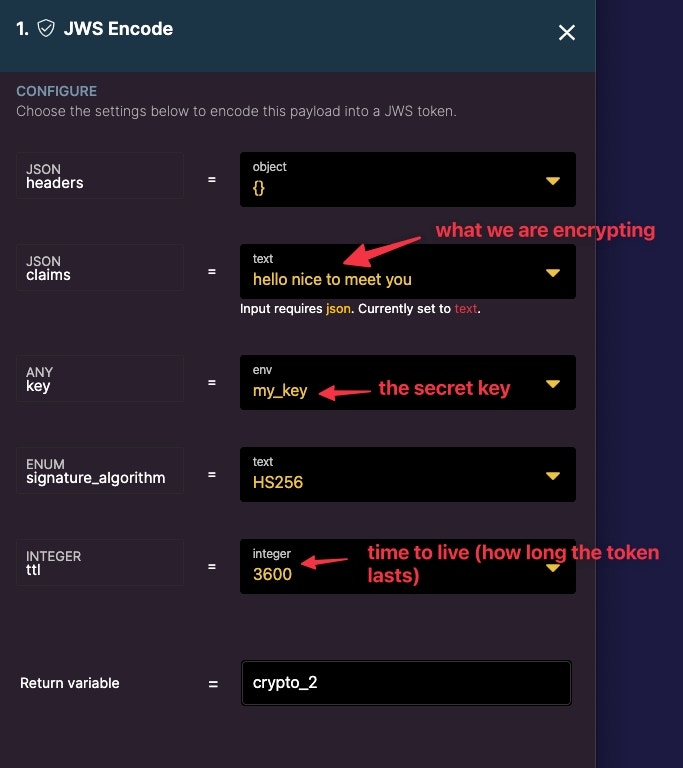
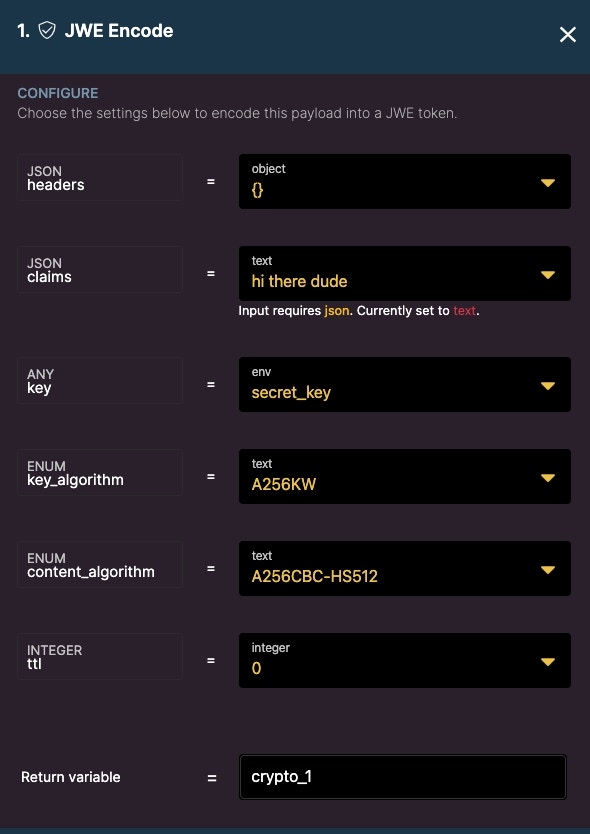
Next, use the JWS Encode function to encrypt a payload. In this example, we will encrypt a simple text string.
Be sure to use the secret key stored in the environment variable as the key.
Optionally add a ttl or time to live if you want the token to expire.
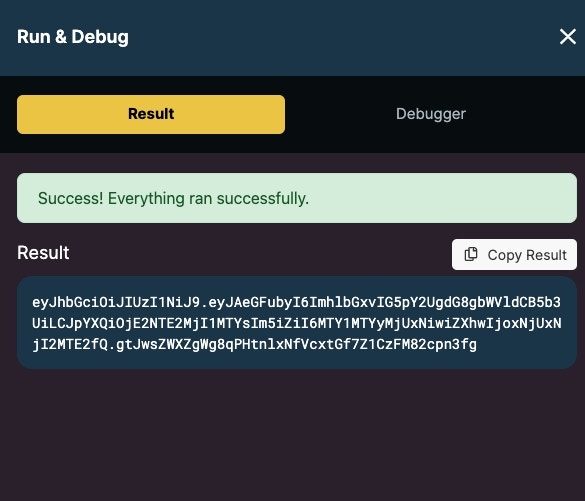
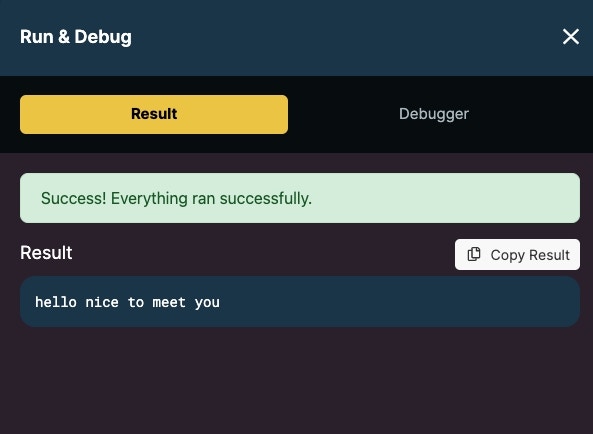
The result is an encrypted JWS token.
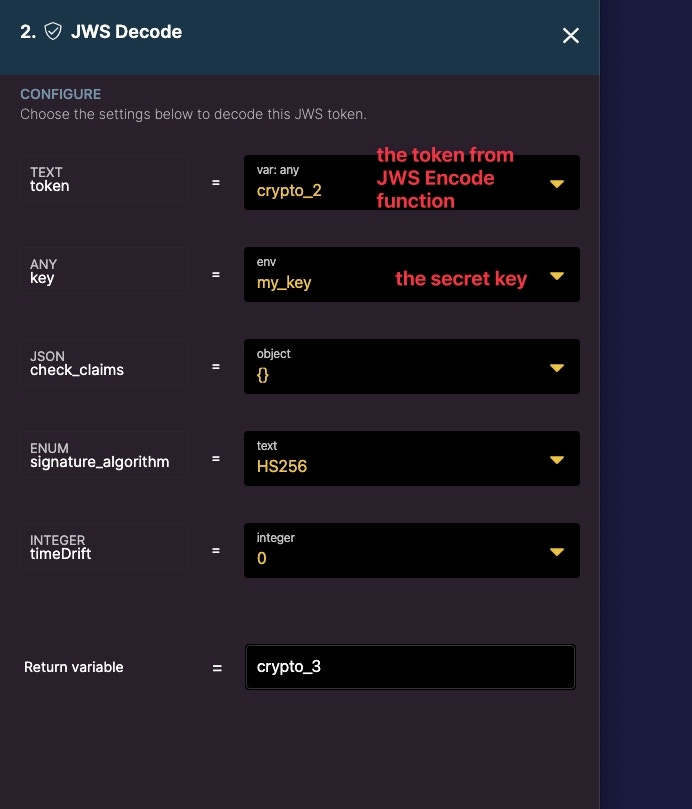
To decode the JWS token, we must make sure to use the same key used for encrypting it.
The result is our decrypted message.
Using an external key
Sometimes you may be using a service that requires you to decode or decrypt a JWS token. Like the above example, it is recommended that you store the key in an environment variable for safe keeping and so that you may call it wherever you may need it in your workspace.
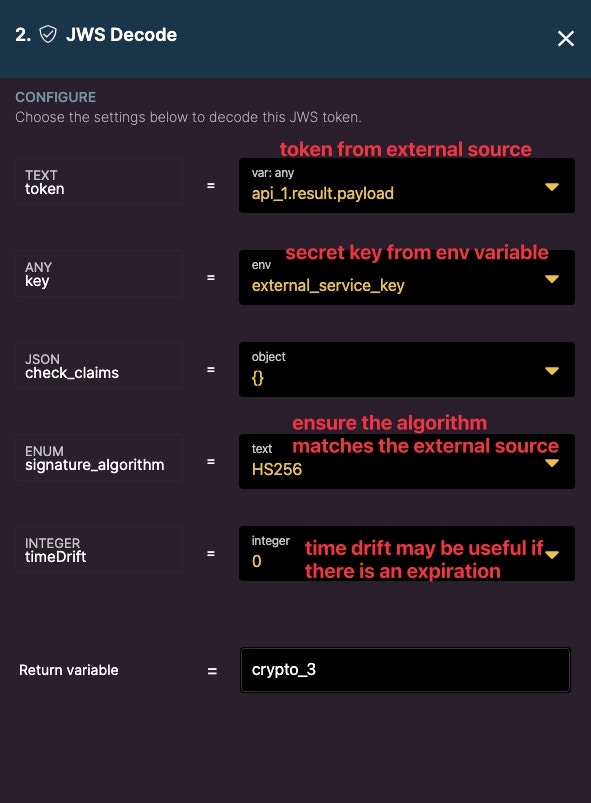
When decoding the JWS from the external source, be sure to use the environment variable as the decryption key.
Ensure the algorithm matches what’s defined from the external source.
Time drift helps account for a leeway if clocks are not aligned. Consider a time drift if there is an expiration on the JWS.
JWE vs JWS
The main difference between JWE and JWS is one is able to be seen but not tampered with and the other is encrypted and not tampered with. JWS is able to be seen (with the right decryption) but not tampered. JWE is encrypted and not tampered with.
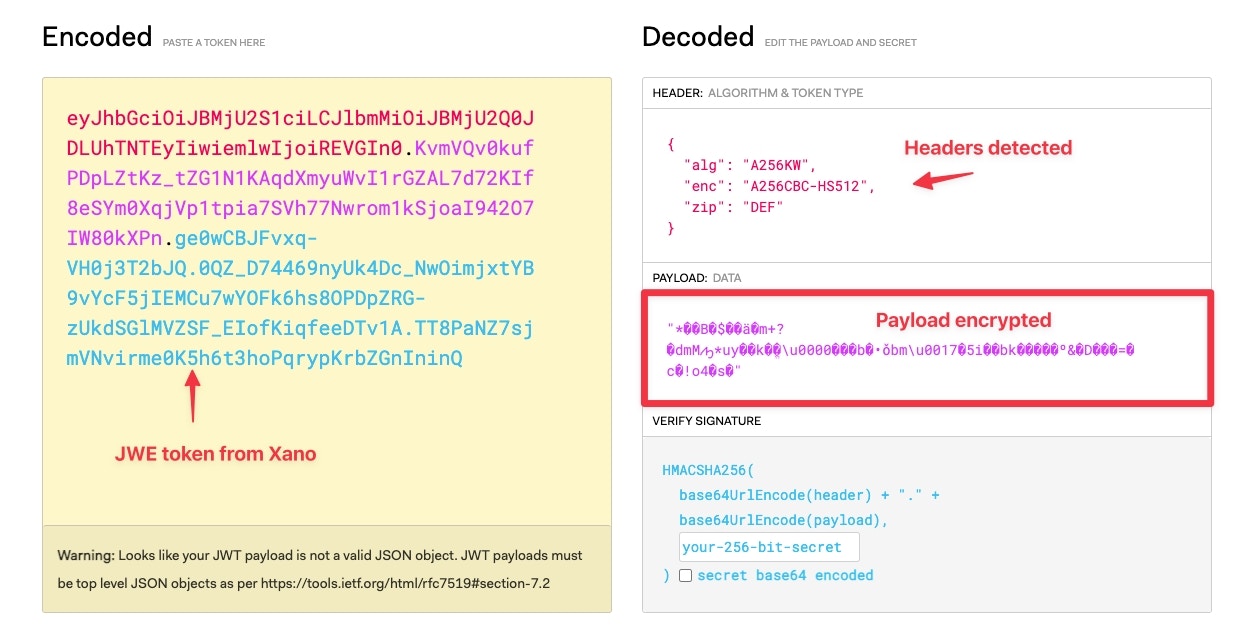
Example using JWT.IO
We can use jwt.io to see an example of the difference between JWE and JWS.
First let’s encode a JWE token.
When we place the resulting JWE token into jwt.io, we can see that the result is an encrypted payload.
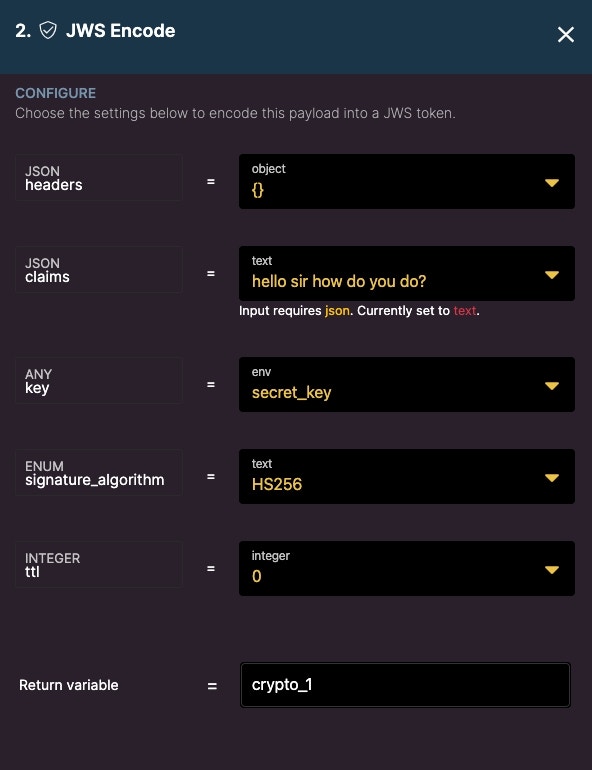
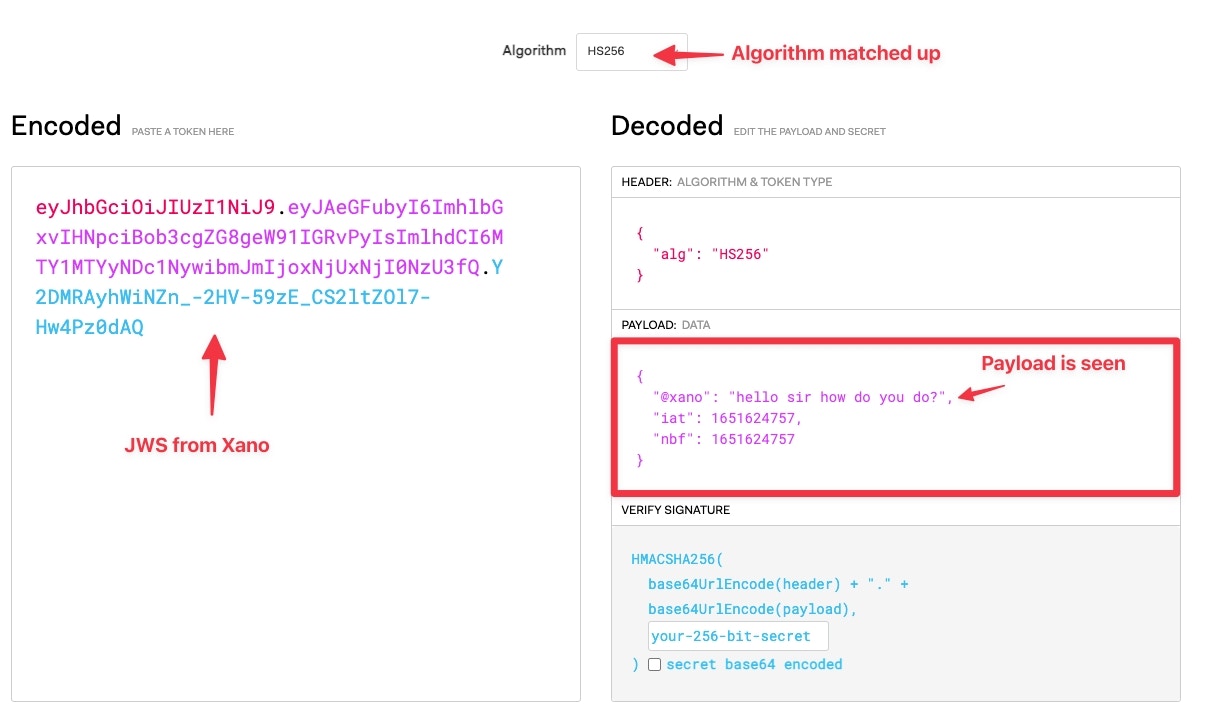
Next, let’s generate a JWS token in Xano.
When we place the resulting JWS token in jwt.io and match up the correct algorithm, we are able to see the payload.